The State of Crypto Scams, Sept. 2022
Learn about the latest crypto scams and how you can avoid becoming a victim in this report.
Artwork by Midjourney.
Whether you are completely new to the cryptospace, or you’ve been around since the days of Satoshi Nakamoto, you have certainly seen at least one crypto-related scam making the rounds. With every emergent and unchartered technology, there will unfortunately always be nefarious actors looking to take advantage of the uncertainty and excitement.
While many scams target the “low-hanging fruit” (i.e. newcomers to the space), even the most skeptical and experienced chainrunners can fall victim with one wrong move.
There is no such thing as a 100% secure system - as a common hacker adage puts it:
If a system is secured by humans, it can be broken by humans.
… And in almost every successful exploit, a human was the weakest link.
Cybersecurity / information security awareness is a never ending game of cat-and-mouse, with new tactics and exploits developed or discovered every day. Staying informed about the latest scams can save you a tremendous amount of pain.
This guide is intended to be a comprehensive overview of some of the most common methods used by cybercriminals to steal crypto assets, as of September 2022, while also staying accessible to a wider, non-technical audience. I intend to also provide periodic updates on the current state of crypto scams going forward, in subsequent reports.
We’ll start with the least sophisticated methods, and work our way towards the more elaborate.
Phishing
Targets: General, Broad
Exploits: Trust, Naïveté, Fear of Missing Out
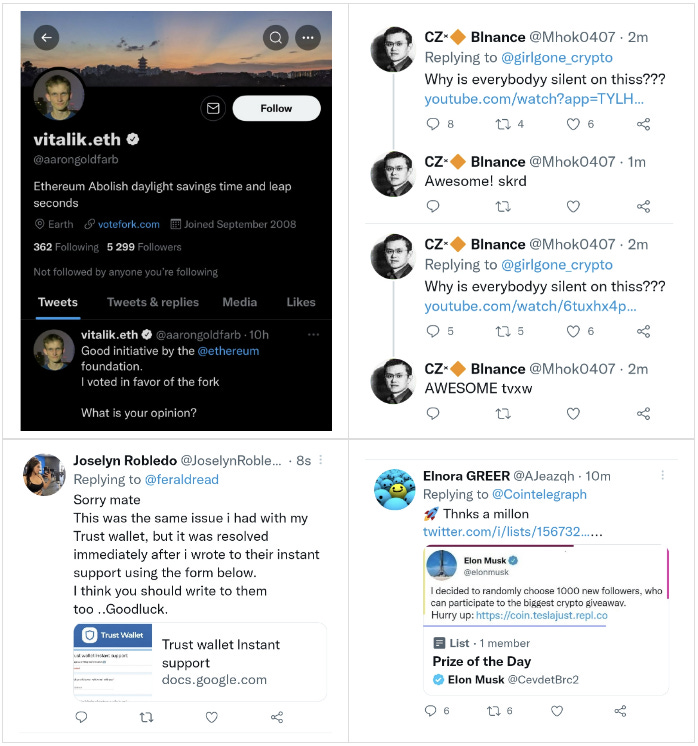
Phishing is a form of social engineering that essentially utilizes look-alike pages or accounts to trick victims into revealing their sensitive information, such as passwords, personally identifiable information, or the master key to their crypto wallet known as a seed phrase.
Phishing involves two elements: impersonation and baiting.
These fake, impostor pages and accounts tend to look virtually identical to the real thing - while often having only the smallest of noticeable differences, such as one letter changed or added to the URL or username. In some circumstances, there are no apparent indications it is fake.
Avoidance
When communicating with someone online about sensitive information, always ensure you are really speaking with the person or organization you believe you are. Double and triple check the fine details. Don’t be afraid to be skeptical and request proof if you are in doubt.
When interacting with any apps or websites where there is a potential to lose your valuable assets, always be sure that you are using the real thing. When in doubt, verify. Cryptocurrency transactions are irreversible and almost always irrecoverable, should you make a mistake.
Never sign any wallet message that you do not recognize or approve any transaction message that you did not initiate yourself.
Never share your seed phrase for any reason, to anyone.
Never click links on social media claiming to offer crypto “giveaways,” “free mints,” “whitelists,” or anything else that claims to offer something for nothing.
Don’t click links in “clickbait” type comments, often containing vague, emotionally charged prompts to entice victims into clicking.
Never click links claiming to “help you” with any crypto-related issues. Bots automatically crawl social media posts for keywords and spam victims with this type of bait.
Examples
Notice: Even “verified” accounts are often compromised.
Unsolicited Airdrops
Targets: General or Specific, Active Users
Exploits: Curiosity, Excitement, Greed, Confidence
Moving on to a more involved and targeted type of scam, we have unsolicited “airdrops.”
Airdrop in this context means to transfer either junk tokens or NFTs into the victim’s wallet.
If something seems too good to be true, it almost certainly is.
The bait in this type of scam is to make the victim investigate. In almost every case, further investigation will lead to some type of phishing site.
In the case of tokens, the token name itself is often the phishing site URL. Once the victim goes there, the scam functions as outlined in the previous section, Phishing.
In the case of bait NFTs, the scam often involves following the airdrop with enticing, high dollar “offers” for it on marketplaces such as OpenSea, LooksRare, and X2Y2.
Attempting to accept these offers will result in a failed transaction, accompanied by a URL and a message saying that the victim must go to the site to “unlock” the NFT for sale (or “allow,” “upgrade,” etc.). This URL is often also linked in the description of the bait NFT collection page. This URL will take you to a phishing site. Don’t go to it.
Avoidance
Do not interact with (transfer) any unsolicited or unknown tokens or NFTs that appear in your wallet.
Do not go to any URL accompanying these tokens or NFTs.
Do not attempt to accept bait offers for NFTs transferred into your wallet without consent (aka spam).
Don’t be fooled by words like “Airdrop,” “Pass,” “Whitelist,” “VIP,” etc.
Examples
Notice: Lower cost “layer 2” or sidechain networks such as Polygon are often used.
Authentic Channel Compromises
Targets: Specific, Active Communities
Exploits: Trust, Excitement, Fear of Missing Out
These types of scams are among the most nefarious because they are often virtually undetectable or practically unpreventable. For this reason, they also have a much higher success rate, and cause more damage.
There will always be unknown unknowns.
Authentic channels can become compromised for many reasons, ranging from software exploits and database intrusions to stolen passwords or data breaches.
Recent official channel compromises have been primarily of social media accounts such as Discord or Twitter.
Another type of attack, known as DNS Cache Poisoning occurs when attackers trick DNS resolvers into caching false information. This is done to make the real URL direct victims to a phishing site instead. This type of attack is particularly dangerous due to its subtlety.
Avoidance
Do not let emotions such as Fear of Missing Out cause you to act impulsively, even when a message appears to come from an official channel.
Be aware of warnings posted by official channels. Often they will say things like “We will never contact anyone directly for any reason.” or “Any announcement of a second airdrop is a scam.”
If something posted by an official channel seems uncharacteristic or suspicious, have patience. Just wait.
If a dApp you have used previously requests a new allowance, do not approve it until you know why, and can confirm that it is legitimate.
When in doubt, wait for confirmation. It is better to be safe than sorry.
Examples
OpenSea’s Official Discord Compromised… - May 6, 2022
BAYC Says Discord Briefly Compromised… - April 1, 2022
DeFi Projects Cream Finance, PancakeSwap Hit With ‘DNS Hijacks’ - March 15, 2021
Convex Finance Suffers From DNS Attack - June 24, 2022
Miscellaneous
For thoroughness, I would like to also briefly discuss some common scams that aren’t particularly technical, instead utilizing deception and/or social status to con victims.
Influencer Scams
There have been, and continue to be, several instances of so-called “influencers” using their social media following to promote dubious cryptocurrencies and NFTs. This can range all the way from the mostly harmless shilling (covert advertising) to the more nefarious pump and dump or rug pull.
Pump & Dump
A pump and dump is when a small, coordinated group of actors intentionally conspire to inflate (pump) the price of an asset, only to then dump their holdings at the top, leaving those outside of the group holding a worthless “bag.”
Rug Pull
A rug pull has much in common with a pump and dump, but may utilize other means of falsely inflating the price, such as only allowing the asset to be bought (and not sold - except by the scammers).
Rug pulls also often involve false promises of future developments to bring in new capital. The term rug pull comes from the nature of the exit - the scammers withdraw everything they can and virtually disappear without a trace, as if the “rug” was pulled out from under the project.
Avoidance
Do your own research. You are reading this now, so you’re already one step ahead.
Question the intentions of anyone attempting to “sell” you on a product/project - what do they stand to gain from it? How are they involved with its development?
Research the history and reputation of any new product/project, especially when there is an unusually high amount of hype around it.
Be skeptical of major hype, sharp rises in price, and refusal to discuss or address doubt.
Examples
Smart Contract Exploits
Smart Contract exploits are attacks that take advantage of flaws in the underlying codebase (contracts) of a dApp to drain as much money from them as possible.
Unless you are a skilled developer, unfortunately, there is likely nothing you can do to prevent these types of attacks.
These types of attacks are almost always completely devastating to the project and community targeted, due to the large amount of capital stolen - on average in the millions or even hundreds of millions of dollars.
Avoidance
Ensure the dApp you are using has performed thorough security audits, from reputable third parties.
If an organization has an active bug bounty program, this is typically an indicator that they at least take the threat seriously.
Examples
Smart Contract Exploit Leads to $300+ Million Hack on Wormhole Solana-Ethereum Bridge - February 3, 2022
Smart Contract Exploit Costs Nomad Crypto Bridge $200 Million - August 3, 2022
Until next time, stay safe out there!
If you found this article useful, please share it with others!






Thanks for writing this up, Daylon! Super helpful and will sure to be of service to many.